

If you own a computer that's connected to the Internet, you are probably aware that there are many risks just lurking around the corner, waiting to strike your PC when it's most vulnerable.
Download CrowdInspect Crack + Serial
However, you can turn to specialized software to prevent and counter these attacks in a quick, efficient manner. CrowdInspect is one of these apps.
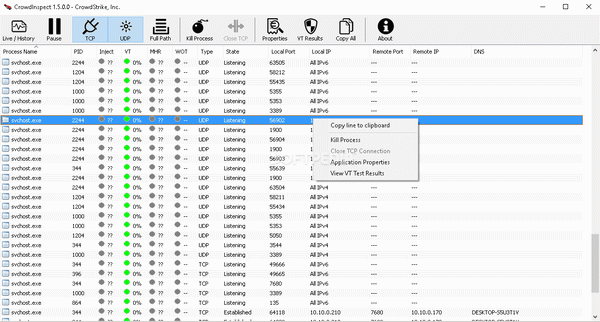
This application lets you view a list of processes on your computer, in order to verify if any of them has malicious behavior and communicates over the network.
When you launch the application, you will be prompted with a window where you can view a brief description of the program's functions and choose between using a built-in VirusTotal API key or a personal one, which can be manually typed.
After you close the window mentioned above, you will be greeted by CrowdInspect's interface, which provides you with a list of processes on your computer along with additional information about each one of them.
You can see the process' name, PID, whether or not it is injected, a VT report, a Malware Hash Registry value (MHR), a Web Of Trust (WOT) rating, the type of communication used, the state of each process, the local and remote ports used to communicate, as well as the local and remote IP addresses.
You can choose to view TCP processes, UDP ones or both by pressing the corresponding buttons on the window. Alternatively, you can choose a live/history view that switches between live processes and ones that were scanned in the past.
Furthermore, it is possible to view the full path of the processes by clicking the "Full Path" button and kill any process with the "Kill Process" function. If you want to view a brief VT report, you can do so by clicking the "VT Results" button.
All things considered, if you want to keep track of what processes on your PC communicate with, you can do so by turning to CrowdInspect. It comes with a simple interface, does not require installation and integrates a VirusTotal API key.
CrowdInspect Review
Read moreokay so in this video we're just gonna have a look into what crown SPECT actually looks like within the duo GUI itself what everything within it means and how it reacts when under the presence of actual malware so it first got the life versus history tab so this is obviously the live feed at the moment of all the process that were running on the machine the history tab will normally flag up events that crown expect believes the user needs to analyze further for example the moment a mulher the first malicious process is detected it on the on the flag up here but it depends on the operating system and the version obviously the pause button obviously just pauses the live feed so you can get a quick snapshot of the system and have a look bird conduct any further analysis you need to what if it if it process a malicious process pops up you can specify or hide the TCP connections or the UDP connections just shared the bet windows processors running running sure the full path to the process which is a good way to capture any suspicious processes that might be held under a different directory for example svchost is always going to be under system 32 who isn't there any other any other directory you know it's probably a suspicious process on delicious going to say kill process does what you expect select any process and use that to kill off the connection and the process on the machine completely you can close TCP connection which would just shut down back to that particular TCP connection the properties tab obviously just gives a bit bit more in-depth information about each process according to the type process that it is VT results is grayed out because we don't have a connection to the virus total server but what that will show against each process it would show the virus total API and all the services that run on it all the anti-malware services including a sha-256 hash you can use against the virus total database if you wanted more information and it will show each service will show whether or not its flight up it's been flight up as a malicious process in the past coffee all just copies the text from this interface you can then copy into notepad and get out and eat salt you can copy out a domain name or an IP address for further analysis about just tells you a bit more involved the tool itself about the manufacturer about the operating systems the versions how it detects thread injection so how it does that how it scores that each API virustotal my last repository work with trust whether available from how their scored as well also slightly different between the three of them and then we've got obviously the columns here listed by process name by default just to make easier for the user I've got process ID which is obviously quite key one if you want to check that against task manager or another service like like pokémon inject shows whether or not green shows whether or not it's been injected sorry whether it's been scanners ejected obviously green and okay mean it's fine it's not injected ? or greyed out just means it hasn't been Scott yet or it can't can't be scanned in the instance of the crowd inspector process itself for our souls obviously greyed out because with notch app it's not connecting to the server all my oh hush repository and web of trust aren't showing anything as there's no malicious instances or events that have triggered Mia but this comms are obviously specifying either UDP or TCP connection on the state of the connection either listening or established the local port and local IP show obviously the the source port and IP address of the each connection it can change between your actual IP address or your loop back or the specific Nick for example if it's if it's a virtual machine remote remote IP or the source IP and reports that the connection is running on sit in this instance Firefox you running through through port 1076 and 1075 and it'll also show the domain name if it can resolve it from the IP which you can again be used for for further analysis so I'll just load up some malware and you'll see our card inspect copes with it okay so we can see straight away this new boss to exe is fight up from the malware hash repository are suspicious so that the 22 scales sorry the scale of the mile hash repositories score and is either grade outs it's either not not malicious or it's been flight up as malicious so see the great all red it's obviously not not injected through itself or any other process that the crowd inspect can can show us here but what it is showing is a different kind of connection so it's sending sync packages through one's going to port 80 to this IP which gives us a domain name it's quite useful because again we can copy out all or show us it pours nope unpause that then yeah do we pause copy all good tune it apart again let's just we can quickly do this in real time while it's picking up these connections and then we've got straight away we've got this malicious domain name here that we can check or if we can check if it's luscious through some third party or open source IP a resolution tool for example Tecna fence have their own called automator which is Python scripting tell you the source of the domain name so it's from it's obviously its IP address but we can already get that from crown inspect whether it's blacklisted or and yeah you can just you can just use it to get any further information that you need so obviously there were but trust is like that up where the trust has a different scoring system so the higher the percentage the better the reputation of the process so of sixty percent flagged up the yellow there any lower down would have been sorry any load on percentage would have been orange and then through to read the same as Marwat hash repository and files total obviously not showing anything because we don't have any connection to the server but that's normally the first one that would flag up alongside my warehouse repository as opposed to disappear in with their with weber trust
.....
| File Size: 618 KB | Downloads: 6104 |
| Added: November 9 2021 |
User rating: 2.5
754
2.5
|
|
Company: CrowdStrike
-
-
|
Supported Operating System: Win 7, Win 7 64 bit, Win 8, Win 8 64 bit, Win 10, Win 10 64 bit |

User reviews
03 March 2019, Marika think:thanks admin
08 November 2018, Antonio think:謝謝CrowdInspect破解
10 September 2018, Donald think:salamat sa inyo para sa crack