

Since most computers are actively connected to the Internet, data is constantly at risk whether or not an antivirus is installed. Security level is never big enough, but it is better to stay as much as possible on the safe side, especially if you handle confidential files. Folder Lock is a powerful tool dedicated to offering that extra sense of security you need.
Download Folder Lock Crack + Serial
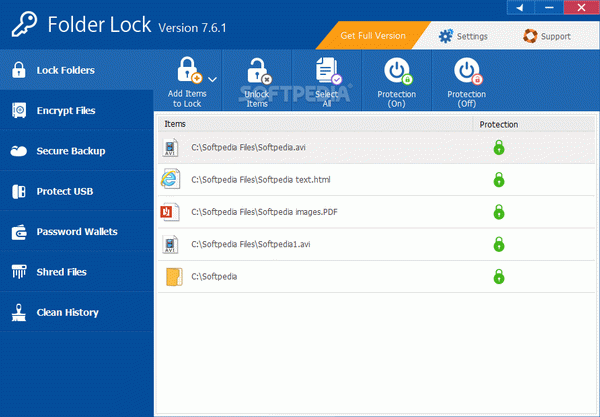
After a quick and uneventful installation process and a system restart so that it can properly function, you can go ahead and bring up the main window. The interface features a modern and visually appealing design, managing to cleverly store major actions in a side panel and the center workspace providing necessary tools.
One of the basic security tools you can access is “Lock Files”. Items of interest can easily be dragged over the main window or located using a dedicated explorer, which also unveils the possibility of locking an entire disk drive.
An additional option lets you encrypt files for even greater security. A so-called “Locker” is created on your hard disk drive where files are encrypted and kept safe.
Moreover, important content can be stored online with a dedicated cloud service. What's more, you can also use a removable storage device or even CD/DVDs as a means to enhance security by keeping your lockers somewhere else other than your hard disk drive.
Last but not least, the application also features support for keeping your credentials safe by creating wallets. There are various card types you can choose from, such as bank account, business info, license and a lot more.
Nearly every step of the way requires a password, which can get frustrating if you're planning to use most available features. However, you can use the same password, but this increases the risk of making your files vulnerable to attacks.
Accessing the settings menu unveils a lot more options to protect items you manage with this application. An interesting feature is “Hack Security” which monitors attempts made to crack your password, with the possibility to exit the application, log off and even shut down the computer if a certain number of incorrect attempts are made.
All in all, Folder Lock is one of the most powerful security tools you can stumble across while browsing the web. It offer so many options to enhance file safety that it is highly possible to get lost in the amount of password requirements and places to store data. However, this can also be used as a means to keeping predators at bay.
Folder Lock Review
Read moreplease turn off the adblock subscribe and share links will be below for anyone wanting to support this channel hello everybody my name is Craig Bennett's and I'm the founder owner a sec fuse nope and today I am doing a review on Folder Lock folder a lot is a program that buff has a trial and paid version into it and the one thing that you need to note right now is if you watched my previous videos you know I try to keep things cheap if not free as possible but I have as high quality into it especially when it comes to cybersecurity and this is no exception now as far as this goes it does have a hefty price tag of $40 or you can get in a bundle with a bunch of odd things and get a little bit cheaper but why would I be recommending something like this with a hefty price tag well it's because he got really worthwhile features into it now while I did get this for free to review I want to mention that I am keeping the price tag in mind and in fact let me get into a little story here just point is little further what photo lock does is it is a file and folder encryption technology and basically basically that just means that you encrypt it and that guys can get into as long as you got a hefty password into it so let's get into hackers if you are famous if you are famous to some degree even my level then you're the exception to this rule because if you're famous the more famous you are the more of risk this is and I'll get a little bit more into this and later but the more you got to do I've been able to hack into high phones and rulers windows phones blackberries retro phones so on and so on and with that that mine I was able to hack into him with battery as long as the batteries into it you met the phone's off itself the batteries into it I can hear everything that's being said in a room and even see out a camera and pull up information depending on the operating system but if you aren't lower-grade like for example my grade where I'm helping you the viewers with cybersecurity and things of this nature many the bad guys are known as black hats many black hats love this and actually try to help me once in a while with this because there's just flat-out not enough people who know about cybersecurity and that they want people to really be involved with it like myself where I want you to be involved with it and to knowledge and to actually be proactive into this one it makes it challenging for them but the bigger reason why is it's a very isolated area and you don't find out if you ever get into this career field or hefty and to hacking you don't find out that it's a very small world a very very small world because there's just not many people who's into it and willing to put their time into it but there is and full office ly that hate what I'm doing and I've even used some of their attacks and some of my videos like fishing tags and stuff of that nature to show you real world example it's so even on my level I have targeted attacks and on your level and given that you're not famous to any degree you're not going to be having a target attacked or at least you shouldn't have a targeted attack and what I mean what is is a targeted attack depending on what exactly they're doing let's not say they take a month to chart you and to actually act upon it that can easily be $500,000 or am an hour right there half a million dollars per man-hour for just trying to target you if you got back credit Horrell credit if there's virtually nothing that can do if it that's half a million dollars out the door that they're not getting back so they're respecting when they target you they're respecting at least half a million dollars so that's a very important thing and obviously that depends on what was thanked what they're doing so when you get attacked if you're just the average Joe it's a mass attack it's it's a lot of people stores might get targeted like Target Walmart and so on and for their credit information but you personally won't and this means that you of your the attacks will be trying to get your identity so dental FB and your legal papers your medical your Social Security your bank statements your tax information things of this nature these are the things are going for because if they can do a mass attack you can grab a bunch of this they can easily go well above the half-a-million dollar and pretty much even go up to a couple million dollars in a small widespread attack and this is this is very important notes because what you have to focus on if you're the average day at a person is how to protect your identity and this is a great method to do it I'll get a little bit more into this why we going through it so let's start this up and as far as this goes this is o1 install it's one thing I want to mention is if you're working on something save it because it wants to restart and for me it just said okay for the button if you press that it will just start restarting right there no real warning besides the message that pops up so keep that in mind that kind of messed me over and that's why I'm marking that as a con I really should have do you want to restart now or later now hey hey let's restart okay No so yeah keep that one of mine but that's you know one time thing so it's whatever now as far as this this is what its gonna look like 1e heavier things setup as far as password into it and this is the master password to get answered the entire thing and if you don't know what this is you're not gonna get into it and you might be asking why is in the recovery method well the only safe method to do that as a 2-step verification and you can't really do that with a localized software that's that's offline at a moment so with this not being connected to the Internet aside from the service backup feature the secure backup feature there's no way for a 2-step verification to properly work and that's important notes now let's get into this real quick Sarah Palin the story about earn you liked her or not don't care she got hacked yahoo account got hacked a couple years back when she was coming for the VP I think it was VP my been something else but anyways basically won't happen him is she is a fast person so again a targeted attacked attacked purely on her stuff and knowing who she was so the hackers obviously didn't know her password so they went to Yahoo and said forgot my password put in her email address and since she's public she they said oh here's her birthday and I said that's correct or something like that I don't know what the security question was but it was something around at that point and they gave that the Yahoo gave from the password and that's how they hacked in and to her email address and that's why you don't want a recovery method within here so put out with Isis for passwords within here get something like the LastPass or something like that and put a note and at least put it where your hint and what the password is if not the actual patcher itself I use LastPass so it's something you have to trust it but for me I use LastPass it's worthwhile to do that if you want to go threaten around otherwise you're risking losing everything forever so as far as this goes let's put it in a wrong password and that's what it looks like let's put in the right password and here we go so as far as that goes if you go into the settings for the acts settings on dialog we can actually see the logs for our logging in so if we select the set increase best or action if someone actually tried to put in the incorrect password and then you can actually tell the whole machine to shut down and I throw so many attempts this worthwhile to note because brute-force attacks someone can try over and over and over and over different passwords and eventually they will get in and this slows it down so much that it won't be worth it keep in mind if you wanted to can enable video then you will know that the by having a few characters more you can go from five minutes to crack a password to nineteen years go for you back and they go to 30 seconds so a couple characters mmm big big thing and when you're slowing it down with something like this that's a huge thing to keep in mind now as far as that goes let's just jump into this so as far as locked files what does this do this uses general level filtering and basically it hides your files pictures music documents so on even if the computers on safe mode it will hide it and with that in mind this this could be used for something like say for example if you had a laptop taking it to a coffee shop you hit your medical files and stuff someone stole your laptop if you have a program like pray or something else and I do have videos on them it there are free programs that you your computer whenever it sees the internet and you tell that program to phone home it will give you the Zach address especially if I had GPS on the device and you can give that to the cops and it will even take the picture to the person who's using it so the person turn that stole it yeah the cops go there right the person get your stuff back and they're you otherwise don't count on getting your stuff back in the meantime you don't have to worry about your stuff being exposed so you don't have to worry about your data being sold keep in mind things like social security's like $50 between $50 to $350 been on the seller things like birth certificates is at 25 to 200 again depends element and his certificate things of that nature so there is some actual value to your information and this helps protect it now and those numbers go up and down I've seen them go up to a couple thousand dollars I see him go down to ten dollars it really goes all over the place so as far as that goes let's go into the next thing and as far as this goes let's go ahead and open this up and basically this is a encrypted file or a folder really and if I try to open it here the thing will go here and ask me for the password because it's encrypted and it's closed now if I put in the wrong password it'll just kick off and say something like Chrome password and if we put in the proper password then what wound up happening is the thing will unlock and I'll be able to do what I need to do with it so this is a this is actually where to meet the software is and what you would do is simply do a crate a a locker tell it where to save the locker itself and then you would set a password and basically it will look like it's partitioning the part of your drive forint and in reality it's actually just encrypting the file and it is partitioning some and what's happening is is when you open it up you can go in full around do whatever you want and what do you want to encrypt it again you can close logger now when you try to shut this down if you have a locker open Locker is one of these with the encrypted stuff then if it's open then it'll tell you don't know no one's open and you need to close it and you have an option to close it this is worthwhile for a major reason if you have something like Dropbox Google Drive or something like that this is worthwhile especially if it's like pictures planned things of that nature a a lot of people don't know this but if you look at the terms of services who owns data that's on a cloud services its the companies they don't really look at the data but they technically own it and this mixtures that it's hidden so let's say that you're in a country that will arrest you because you're wearing color blue well basically this is the one thing that could protect you the government and also could protect you from the company itself from getting into your information and the one thing to keep in mind for something like this is you need to have your stuff the the program Folder Lock on both sides so like all your computers and also on top of that you need to make sure that you close the locker because otherwise it won't be encrypted so with that let's go into the next thing and this is the secure backup this goes a step further and this is the company's own cloud services now as far as this you might say wait wait a second you're still recommending is even though you gave a free solution why would I do this well the if you end up doing this method to encrypt your stuff going across like Dropbox or something like that then whatever vies is don't do that necessarily with your identification papers medical legal tax whatever use the surface like this and pacifically this service because what happens is is this actually encrypts both the actual transmission it also encrypts the file itself so the transmission is encrypted with 128-bit SSL connection this is both the login and the entire transmission and with this you'll have the ability like any other backup service to restore or delete things that just nature it's pretty basic on that front but the one thing that they keep in mind is what is being moved disease occurs and and with that in mind you have a double layer encryption the transmission plus the actual 256 a yes and keep in mind if your password on the stuff you know the ik rip ssin is high and the highest and it can be if your password sucks then it will take him five minutes and break in if your password is great and encryption sucks then still take them five minutes and break in but the password is great and encryption is great it'll take them years for a 256 AES it will take them ten thousand years to break in with current day technology and as you can see from my Cain and Abel if they did it just a flat-out brute-force attack with the password alone and they were allowed to do that then you can see that by just adding in couple characters you automatically add quite a few years like two decades easy so that's why it's important to realize that that's why it's important to realize this that you have a double layer of encryption and this is worthwhile in my opinion from tax documents medical forms things that again identity theft what you as the average data use your be target for obviously if you're famous this still will be useful in some aspects because identity theft is even more so on your side people want your stuff so let's go into the next feature and this is also worthwhile so the biggest features I see on this on the program that people will want is the encrypt files and this and what this does is you can actually encrypt attachments you can email attachments and stuff at and that way and the transmission it's encrypted now as far as that goes let's go to this so if we're email it says zip file and let's go right here I made a zip file earlier and if we right-click it and go to 7-zip open archive and then open up a little bit more you can see it's encrypted it's method and if we try to extract it we need to put in the password and if we put in a proper password the thing will start encrypting if not it'll say that so as long as the person that you emailed this to knows what the password is then they can actually go in and unencrypted it and go from there now as far as the other you can have an executable file for this you do need to have the Locker closed and for this you need to you don't need to have USB attached or CH ends you can actually create a brand new locker if you want but if you want to use one you do need to have that close and good next to what locker use what designation to leave the file and then you can give two Pat's ready to give it a try thing let's open up this this is the one I made earlier for this example so we can keep things speed up and and basically as you can see here they will say now just wait a second or two and yeah hi hey ves was actually me false positives on this but as far as that goes you can see that it opened up a brand new program and I can put in the password here and unlock the locker at place with an executable why is this important well what happens is if you're sending this off to someone you don't want them to have to download this and this is a huge problem that you'll find with many encryption things is it wants you to download the exact same program and the person on the other end doesn't they just want the stuff and they are just putting over there crap with sending the encryption or they understand and they want these be encrypted but they still don't want to have to download a given software and add it to their category so what this allows the person to do is you can make it into a suitable file and the person on the other end they just need to know the password put in a password and they could get in just like before so with that let's move on to the next one and finally I'll mention wallet so what is wallet well basically a wallet is is as it sounds and basically the it keeps your credit cards bank card stuff ahead it's what as futures I was talking about that it's a yeah it does this job but I've seen it and so many programs now I'm just about every single Krypton program that I just want to bypass this but for quick clients it's just you give it a name give it a whatever password everything to match one when it's tough it's done you can tell what car do you have and it fill out information and go from there again I seen on so many things they've got LastPass you already had this we've got one pass you already have this there's many programs where you could easily already have this and not even realize it I I don't I don't ever use these so I'm not really good to say that's worthwhile or not personally I'll just say no but it's up to you it's good to shred files and this is a narrow one as for you this could literally be at the only choice for you but for me and if you got a vast or lease my version of a pass then you do have other choices so what data is shredder do or a fish render there's a ghost fisherman sure I fonts whatever what it does is you can actually go and shred files and you can tell what to shred and that's open to the settings and what to replace this stuff with so in case you don't know forensics if you delete something off the computer it's not truly deleted basically its earmarked so the operating system does it can right over that space on a CD the the table and basically what happens is when this stuff fills up it will start writing over those earmarks in about seven eight times but right over it you probably won't see what was there but it does take quite a few times and you might never be able to really erase all the stuff there so the only way to really do it is by using a method like this the thing I see where the pitfall on this is the amount of times you can do it with a vest you can tell amount of times yes you got a life of choice of what you can do but you can tell it a billion times well not doing but a hundred times or so if you want keep in mind if it takes ten minutes and do one pass times that behive whatever in and that should give you an idea that it's going to take a long freakin time and doing something like 10 passes it's good enough but if you want to be real thorough like myself 100 passes is something I do unfortunately you don't have this choice within here so there's not much you can do about that besides like what type of information you want to cover on the table so with that let's go into the next clean history again this is a because even Microsoft has things that does most of this many programs already do this for free and it's not that hard to do it yourself there's some use here if you want to be quick and easy if you don't have it early but you probably already have a free way to already do this what the meat of this is is really lock files encrypt files secure backup and protect the files in a CD or gzip formats so that's a very important to note the wallets the shred files clean history I don't see that being worth while and that's where I'll say it's it's not something jump virtually for those three features but for diversity's especially the Crypt files and this one that is something to jump for joy and that's why I recommend this so the cons you probably are note pros the cons of this again when you first install it you have to do a full restart and there's not really much of a warning the other con to this is the if you do use the shred files you can't pick how many passes you have like for example if I go and shred that I mean like if I want to shred dad I can select that and the shred and it will give you a warning and basically you're not gonna get it back so for press yes so just short shred it and go from there and it's that simple but like I said I don't know how many passes it went through and this is something important to note oh and the other and last con is the price itself is up there but like I said it's at one time and these to me make it worthwhile it's up to you if that's worthwhile to you and there is other methods out there putting like I said the other systems that I use that they're so complex even it's something I love it's not that they're complex the user interface it's so horrible on some of these other systems that you can't use it we're on this it's pretty user friendly like there's not too much more we can do for as far as the usual friendly so this is worthwhile in that aspect alone but it was oh and it's reliable and the company's still updating its defiance that's that's another thing that's prom that you will run into when you get into Krypton software but anyways I'm pretty sure this videos run long enough and you probably have an idea of if you want it or not and and you know my opinion on it now if you like this Knievel look like subscribe share and also check out our patreon campaign and donate to us if you don't like this come the dislike and tell me why I could fix it in future videos but if you do have any questions on this or anything else or any comments that you want to have going that in comment section if you have tried this leave it below your thoughts on this so other people will know what you think about it and they can get more than a forum opinion since multiple people be telling them about it good batter and effort go and leave your opinion down and be thorough and be detailed as possible and that way people know what to expect again it's been great back found an order text me just open up you have a great day you
.....
| File Size: 9.7 MB | Downloads: 480153 |
| Added: April 30 2022 |
User rating: 3.8
2368
3.8
|
|
Company: NewSoftwares.net, Inc.
-
-
|
Supported Operating System: Win XP, Win XP 64 bit, Win Vista, Win Vista 64 bit, Win 7, Win 7 64 bit, Win 8, Win 8 64 bit, Win 2003, Win 2008, Win 10, Win 10 64 bit |

User reviews
August 23, 2018, James think:Baie dankie vir die keygen Folder Lock